Reverse Engineering Android Apps
1- Getting APKs from a device
First, find the package name of the application you want to download. You can list all third-party packages using:
1
adb shell pm list packages -3
Next, we have to get the path to the APK. This can be done using:
1
adb shell pm path <package_name>
Now we can just pull the APK from the phone:
1
adb pull <path_to_apk>
2- Using apktool d <path_to_apk> we can extract APKs.
Note that apktool will not just simply extract the .zip of the .apk: It will also “baksmali” (disassemble) the embedded classes into smali bytecode.
You can also explore the AndroidManifest.xml to see what activities & more the app exposes.
When you see that is there exported activity try to start it direct using adb:
1
adb shell am start <package-name>/.<activity-name>
3- When you edit in any file such as Androidmainfest.xml for example you edit activity to make it exported, you must align and sign this apk using uber-apk-signer :
- apktool d <.apk>
- make your edit in the apk folder
- open this folder and run this: apktool b
- then run this: java -jar uber-apk-signer.jar -a /path/to/apk
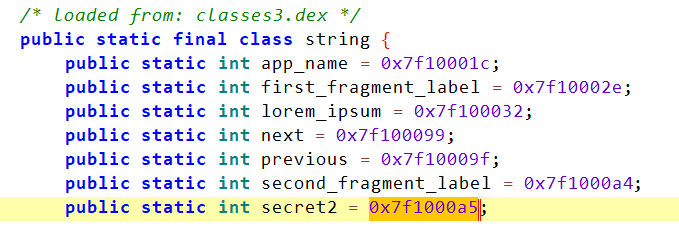
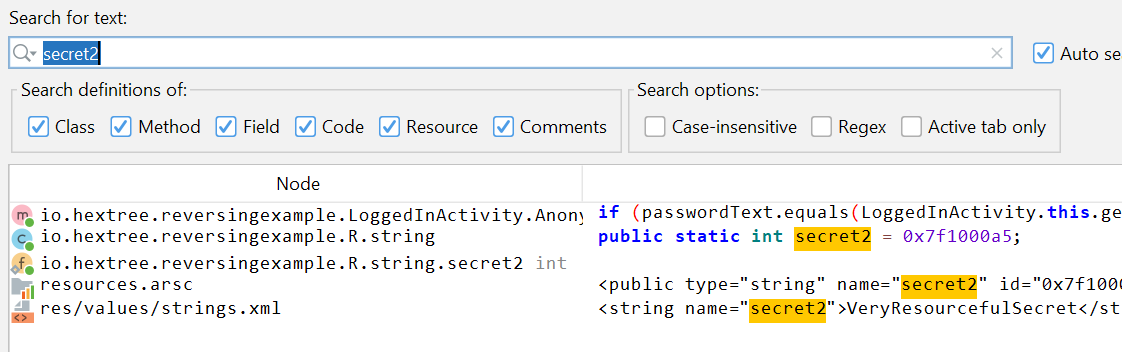
4- Strings in Android applications are often not hard-coded, but instead packed into resources. If you see code such as R.id or R.string it means that a resource is loaded from the resource directory or the resources.asrc file.
This highlight the id for string “secret2”:
you can search by string or by their id:
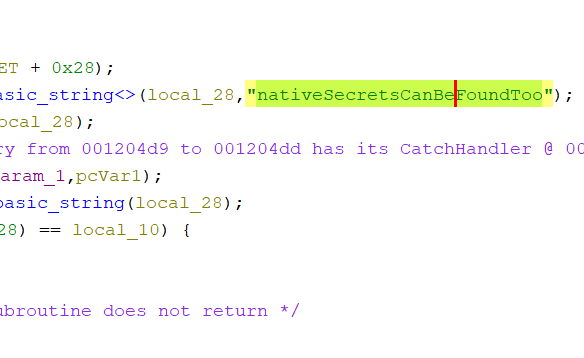
5- Some applications will use functions implemented in native shared objects. You can identify calls into such functions by the keyword native.
This functionality is called JNI - Java Native Interface. Jadx does not let us decompile shared objects, instead we need to use tools such as Binary Ninja or Ghidra. You won’t have to do that for this secret though - using a tool such as strings should be enough to find the password!:
6- If application Used API to request data try intercept this action and see what can do with this API.
Try to read the source code if this API key loaded from native library —> .so and search about it using Ghidra or Strings Tool in linux.
7- If the application has updated version their is extension in vscode to compare changes in two versions:
Compare Folders extension for Visual Studio Code to check the differences between the original Hextree Weather app and another updated version. This allows us to quickly navigate differences between the two applications.
We use the jadx CLI to decompile the original and the updated APK into two different folders, and then compare them in VS Code.
THANKS FOR READING ❤️