Hack Like a Ninja: The Art of Idle Scans with Nmap
When it comes to stealth in penetration testing, few techniques rival the efficiency and subtlety of the Idle Scan. This advanced method allows security professionals to gather information about a target without ever revealing their real IP address. By cleverly using a zombie IP, the scan appears to originate from a third-party system, leaving the attacker undetectable.
How Does the Idle Scan Work?
The Idle Scan technique exploits the behavior of predictable IP ID sequences in certain systems. By analyzing how the target interacts with a zombie system, attackers can infer information about open ports without any direct interaction between their real IP and the target.
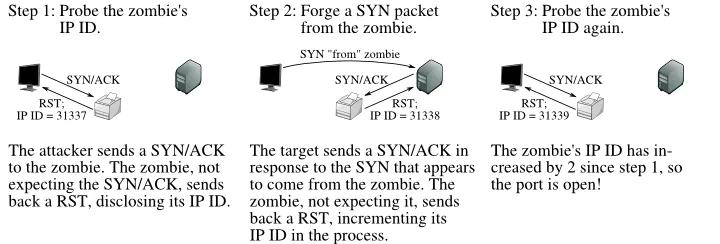
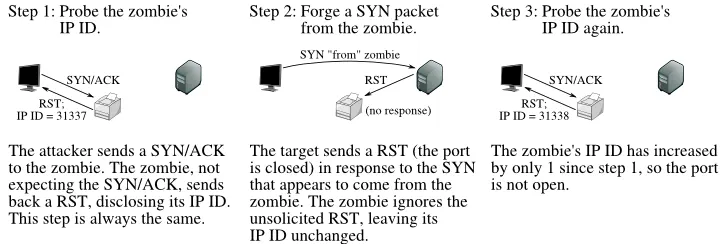
Step 1:
Step 2:
Step 3:
Example Using Nmap for Idle Scan
Here’s a practical demonstration of an Idle Scan using Nmap, the go-to tool for network scanning:
1
nmap -Pn -sI 100.x.x.1:35 100.x.x.2 -v
Command Breakdown
-Pn: Prevents pinging from your real IP to avoid detection.
-sI: Activates the Idle Scan mode.
100.x.x.1:35: The “zombie” IP and port being leveraged.
100.x.x.2: The target IP address to be scanned.
-v: Enables verbosity for detailed results.
Why Use Idle Scan?
This technique offers several key advantages:
- Stealth: Your real IP is never exposed to the target.
- Anonymity: The scan activity appears to come from the zombie IP.
- Efficiency: Ideal for bypassing intrusion detection systems (IDS) and firewalls.
Conclusion
Mastering the Idle Scan is essential for ethical hackers aiming to achieve stealthy and efficient reconnaissance. Tools like Nmap empower cybersecurity professionals with the ability to uncover hidden insights while maintaining anonymity.
THANKS FOR READING ❤️